Are you looking for the best way to send encrypted files from your business applications?
Our encrypted file sharing service enables top companies like Vocera and Plus500 securely exchange files within and outside the organization.
It’s important to make sure your corporate data is transferred and stored securely to avoid data breaches and achieve compliance. Encryption keeps file transfers within and outside the organization secure.
FTP, Standard Email and Consumer File Storage Apps Put Corporate Data at Risk
Many organizations are still using outdated and insecure methods to transfer files, including FTP, email and free consumer file storage apps. These methods do not encrypt files out-of-the-box.
If you use these solutions to transfer sensitive information, that information is at a high risk of being retrieved by cybercriminals. Transferring files without encrypting them also violates common data security standards and requirements.
Send Encrypted Files from Any Device
So what can your business do to encrypt all file transfers on any device? Adopt a managed file transfer (MFT) solution.
Thru is the best solution for your file sharing needs. With Thru, your company can easily send and share encrypted files from your existing business applications and devices.
There are two big advantages of Thru over other file sharing services:
- The number of endpoints you can send encrypted files through
- The flexible integration capabilities
Here are some of the endpoints you can use:
- Web browser application (desktop and mobile)
- Email add-ins (Outlook)
- Business applications (Salesforce)
- SFTP/FTPS clients
- Third-party applications with our APIs
Thru’s Connector for Outlook to Transfer Files
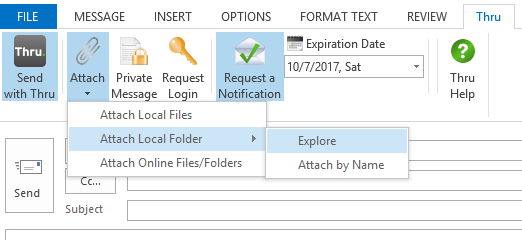
The image below shows what our connector for Microsoft Outlook looks like. This connector is popular because it allows users to send encrypted attachments (both files and folders) from within Outlook. It also has a side panel feature for users to access and view files they have stored in Thru. Users simply open a new email and click a button to send encrypted files.
When files are sent from our integrations, they are uploaded to our servers in the cloud. A secure link is sent to recipients so they can securely download the encrypted files or folders.
Senders can choose to require recipients to log in and download the files to prevent files from being forwarded. They can also attach an encrypted message that can only be viewed by the recipient. After recipients download the files, senders will receive a “read receipt” email.
Thru Securely Transfers Files
Some of Thru’s other security features and capabilities that make us one of the leaders for secure file transfer are:
- Full audit tracking for file and user activities (with reporting)
- Rule-based alerts
- Single-Sign-On (SSO) authentication via Thru Active Directory SSO client, integration with SAML 2.0 Identity Providers, and Azure Active Directory integration
- Managed firewalls and intrusion prevention systems (IPS) that monitor network activities for malicious patterns
- Thru Dropbox™ tool for external users to upload files securely without having to register for an account
