For companies, keeping a detailed log of file activities is a necessity. Tracking the deletion, editing and transfer of credit card information or health records is vital in the event that records are lost or stolen. But knowing the “who, what, where and when” of users accessing enterprise data can be complicated especially with the large amount of cloud secure file sharing applications being used.
Fortunately, Thru has built-in tracking security features to view detailed activity logs of all file transactions. In this blog, we will show you how actions within shared files can be monitored from Thru Web.
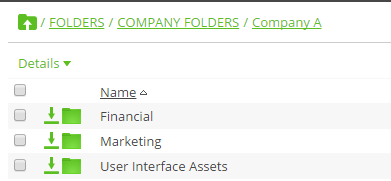
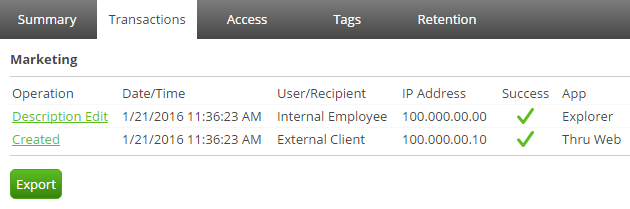
In the image below, you can see that Company A has three folders in Thru created for Finance, Marketing and UI Assets. These folders are each shared by internal employees and external clients who have access to upload, download and edit information. By selecting a folder, a user who has been granted access can view all transactions with record of date/time, IP Address and what application was used. The example below shows two transactions made by an internal employee and an external client who both share files within the Marketing folder. This is very beneficial for project teams so that all actions can be easily referenced in the event of a lost or deleted file. Users can also easily run reports on transactions for files and folders by clicking on the Export button (as shown below).
One company that greatly relies on secure monitoring file sharing activity is architectural design firm HKS. As in the folders showed above, HKS has shared folders within their system for multiple different projects around the world. Since architects and building contractors both access the same folders, tracking each transaction helps to keep a single source of truth, a crucial need for large-scale architectural projects.
