In just 3 years, from 2019 to 2022, spending in the cybersecurity industry nearly doubled, increasing from 40.8 billion USD to 71.1 billion USD, according to statista.com. This is encouraging for anyone working in cybersecurity since organizations have put their money where their mouth is and prioritized cybersecurity. Unfortunately, simply spending more money on security software is not enough.
An important piece of the puzzle is access controls—specifically, what software or entities should users be able to access? That’s where role-based access controls come in.
What is role-based access control (RBAC)?
Role-based access control (RBAC) is closely related to the principle of least privilege (PoLP). This cybersecurity principle states that users should have the bare minimum of access and privileges needed to do their specific job. When role-based access controls are in place, users—whether external or internal—only have permissions to access, perform actions or administrate in specific areas of a company’s digital infrastructure.
In practice, RBAC could look like this breakdown of roles with example access points:
| Role | Access Examples |
|---|---|
| Customer |
|
| Finance |
|
| Human Resources |
|
| Marketing |
|
| Partner |
|
| Sales |
|
| Software Engineering |
|
What are the benefits of role-based access control?
The biggest benefit of RBAC is stronger security of the company’s data. Because each account has limited access to specific applications, environments or corporate entities, a hacked or compromised account (or simply a disgruntled employee) can do less damage to a company, its employees, its customers and its reputation. If a cybercriminal gains access to an account with RBAC in place, the damage they can do is limited to the specific entities it can access and not the entire infrastructure of the company.
Other benefits of adopting RBAC include
- Improves compliance to industry standards and regulations regarding privacy and confidentiality of data.
- Lowers costs for software or tools that charge by usage or number of users.
- Reduces redundancy and interference between employees and teams from different departments.
- Minimizes mistakes since employees can only access what they were trained to use.
- Keeps employees focused on the tasks they were hired for.
How does role-based access control work in Thru?
Thru is a cloud managed file transfer (MFT) solution that includes RBAC as part of its security posture. Administrators are able to control access based on a user’s role, which is configured in the GUI admin section or via APIs.
Automated File Transfer Roles
In our automated file transfer admin portal, we initially implemented four user roles:
- Instance Admin: Given access to all features and settings, including ability to create and manage users.
- Instance User: Given access to all features and settings, except for the ability to create and manage users. Additionally, they cannot change instance wide settings.
- Org User: Requires association with at least one organization. Access and functionality are limited to reading that organization’s configuration data and uploading / downloading files to the associated organization’s flow endpoints.
- Org Transfer: Requires association with at least one organization. Access and functionality are even more limited than an Org User’s.
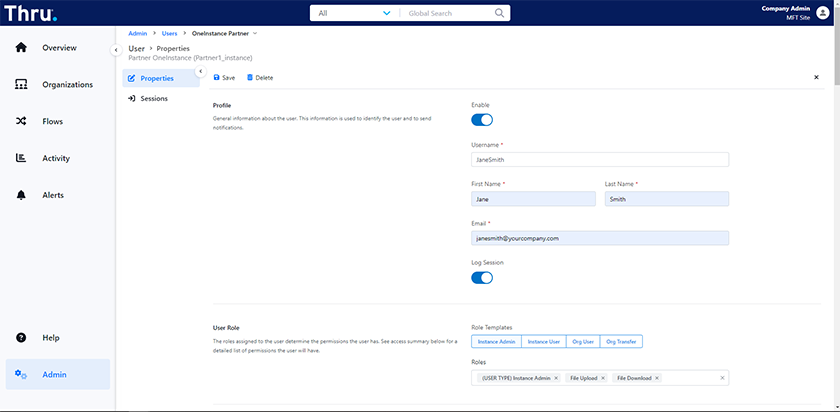
System Roles and Granular Permissions
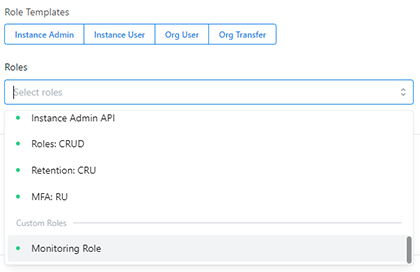
Additional system roles are now available. The roles for a user can be specified by clicking on one of the role templates or selecting relevant roles from the dropdown list. See our two examples below:
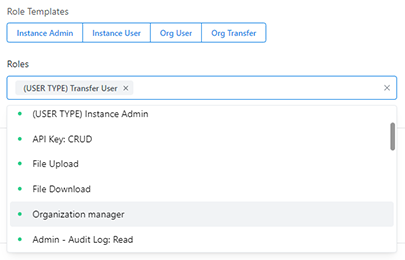
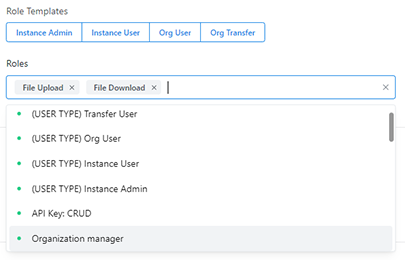
Furthermore, admins can create new roles by assigning desired permissions from the available list. For example, in the screenshot below, a custom role named Monitoring Role was created:
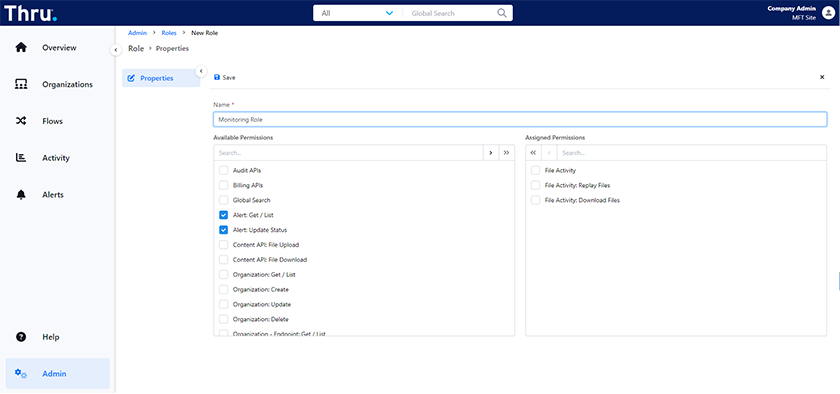
For more information, see our user guide about Granular Permissions »
Ad Hoc File Sharing Roles
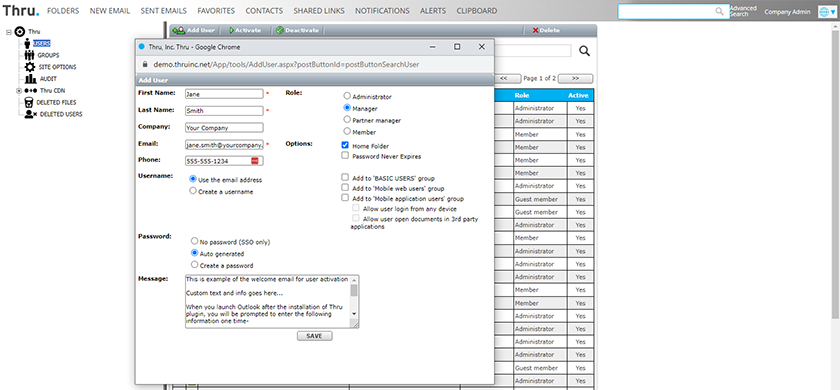
Our file sharing portal also has administrators choose from four roles:
- Administrators have all the privileges to the site and can maintain the site.
- Managers have the option to manage the users but will not have permission to change the site options.
- Partner Managers have the ability to access the administration portal and manage users within the same domain.
- Members can only access their own individual home folder and cannot navigate to the administration options.
Group Permissions in Ad Hoc File Sharing Portal
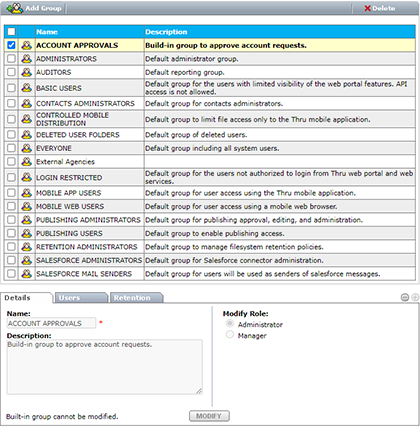
Numerous default/built-in groups are available to manage different parts of the Thru file sharing system. Administrators can provide a user with additional capabilities and limitations by assignment to any of these groups. New groups, such as a Sales group for all sales representatives, can be added and their roles and capabilities defined by the admin.
Beyond RBAC: Thru’s Zero Trust Security Strategy
Role-based access controls help prevent unauthorized users from modifying endpoints or accessing data in Thru’s cloud MFT service. However, Thru doesn’t stop there. We incorporate multiple levels of security—cloud infrastructure security, application security and data security—so your files are always protected.
Learn about the additional measures Thru takes to ensure data security by going to our secure file transfer page »
[Note: This blog was first published on October 27, 2021, and continues to be updated to align with current product offerings.]
