In 2022, 60% of corporate data resided in the cloud—double the percentage in 2015.¹
By the end of 2025, 181 zettabytes of data are projected to be created, captured, copied and consumed globally.²
This shift has made secure file transfer a mission-critical function across industries. To manage risk, ensure compliance and maintain operational resilience, organizations must implement robust audit logging and real-time monitoring capabilities. These tools provide the visibility and accountability required to safeguard sensitive information and support regulated business processes.
Explore key concepts, benefits and challenges of audit logging and real-time monitoring in secure file transfer environments in the following sections:
Understanding Audit Logs and Real-Time Monitoring
An audit log, also known as an audit trail, is a chronological record that captures detailed information about events and user activities within a system. In the context of secure file transfers, audit logs track critical data such as
- When: Dates and times of events on files.
- Who: Username, IP address, location and other identifying information.
- What: Actions performed such as upload, download, modifications, sharing and deletion.
- How: Method of access (e.g., application, browser, interface)
Key Insights from Audit Logs
Audit logs serve as a critical historical record that enables organizations to monitor and identify a wide range of activities and anomalies. These include unauthorized access attempts, suspicious behavior and potential policy violations such as fraud or misuse. Logs also help pinpoint the origin of errors, track file delivery timelines to meet contractual obligations, analyze access patterns and volume and capture key events that support revenue recognition.
From Reactive to Proactive: The Power of Monitoring
While audit logs provide a detailed record after events have occurred, monitoring delivers real-time visibility into system activity. This includes
- Actively tracking file transfer progress and performance
- Alerting teams to failed, delayed or interrupted transfers
- Identifying unusual activity patterns or performance issues in real time
- Supporting operational uptime and SLA adherence
Together, monitoring and audit logs give organizations a comprehensive view of file transfer environments. Monitoring enables immediate response and optimization, while audit logs provide long-term accountability and reporting—both essential for secure, efficient operations.
Top Benefits of Audit Logging & Monitoring
Implementing comprehensive audit logging and proactive monitoring in your file transfer operations offers several key benefits:
- Monitoring and Troubleshooting: Quickly detect unauthorized access, failed transfers, processing errors or unusual activity patterns, helping both security teams and operations teams take fast, informed actions.
- Compliance: Meet regulatory requirements such as HIPAA, GDPR and PCI DSS by maintaining a complete history of data transfers and activity.
- Incident Response: Provide forensic evidence to identify the scope and source of a breach.
- Operational Insight: Help teams understand the company’s file data usage, including workflow bottlenecks, to improve process efficiency.
- Revenue Recognition: Track document delivery dates and milestones to validate contract terms and support accurate, timely revenue recognition.
Challenges of Monitoring and Audit Logging in File Transfers
Enterprises typically manage two primary types of file transfer transactions: Automated (machine-to-machine) and ad hoc (manual or person-to-person). Both present unique challenges when it comes to maintaining visibility, ensuring security and generating complete audit trails.
Monitoring and Auditing Automated File Transfers
Automated transactions are system-driven exchanges—such as scheduled scripts or integrations between SFTP servers or other backend systems—that move data based on pre-set rules or triggers. These transactions can be difficult to monitor and audit due to
- The variety of transfer protocols involved (SFTP, FTPS, HTTPS, etc.).
- Limited or inconsistent logging capabilities across systems.
- Lack of centralized visibility into transfer status, errors or delivery confirmation.
Without real-time monitoring, issues like failed transfers or delivery delays can go unnoticed. Without audit logging, it’s difficult to reconstruct what occurred during or after a transfer—especially during compliance reviews or incident investigations.
Monitoring and Auditing Ad Hoc File Sharing
Ad hoc transactions are initiated manually by users—for example, sending files to clients, uploading documents to the cloud or downloading reports to a device. These are harder to control and track because
- Users may rely on a mix of tools (email, cloud storage, personal apps).
- File activity often happens outside sanctioned systems.
- There’s typically no unified monitoring or logging across these disparate channels.
This fragmentation limits an organization’s ability to enforce policies, detect security risks or maintain complete audit trails for compliance or internal reporting.
Visibility Tools for Secure File Transfer
To effectively monitor file transfers and maintain accurate audit logs, organizations need enterprise-grade managed file transfer (MFT) solutions—not piecemeal tools or disconnected systems.
Thru is a leading cloud-native secure file transfer solution that delivers both real-time monitoring and comprehensive audit logging across automated system integrations and user-driven file sharing. Whether you need to detect failed transactions, investigate file access history or validate delivery timelines for compliance and revenue recognition, Thru provides the visibility and control you need—all from a centralized interface.
Tracking Automated File Transfer Activities
Thru allows automation of file transfers between storage repositories (e.g., FTPS, SFTP, Amazon S3) and keeps an audit of all transactions. The audit logs can also be compiled into different reports and filtered by users, groups, application used, date and time and more.
The Activity view within Thru’s automated file transfer portal displays the file transfer activity for every Flow, Organization, Endpoint and Flow Endpoint in your instance of Thru. In this view, you can
- Search for specific file transfers by flow, organization, endpoint or flow endpoint.
- Select one or all four to get a more granular view of your file transfers.
- Choose from numerous filters to narrow your results to see a snapshot of a specific file transfer.
- Click on the linked organizations and endpoints to quickly troubleshoot and make changes to their configurations.
- Click on the state in Last State Update column to open the Transfer Status Details window.
- Export the results of the activity page to a .CSV file.
For more details, refer to our Thru MFT User Guide: Activity »
Tracking File Sharing Activities
Easily track and monitor all file transactions on a single platform in the cloud via the powerful Thru Audit feature. Thru’s out-of-the-box integrations with your existing email and business applications, such as Outlook and Salesforce, enable users to send files of any size and all activities are recorded in Thru Audit. Thru Audit allows you to search and sort on a granular level for reporting.
Within Thru’s file sharing administrator interface, audit all file transactions such as access, uploads, downloads, messages and storage usage. The following screenshots illustrate how Thru Audit displays detailed transaction history and usage metrics:
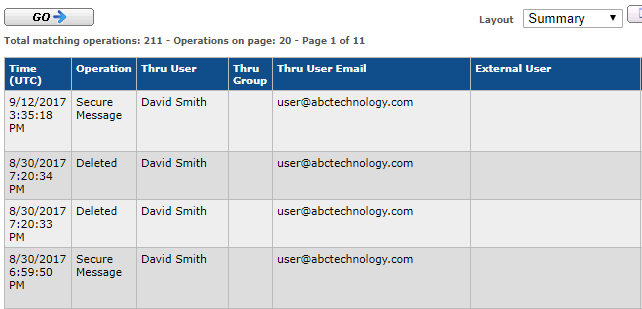
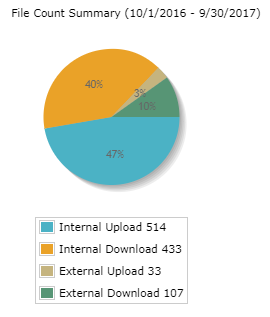
For more details, refer to our File Sharing Administration Guide: Reports »
Power Your File Transfers with Visibility and Control
In an era of exploding data and stringent compliance demands, monitoring and audit logging are no longer optional—they’re essential! By implementing both, organizations not only strengthen security and ensure compliance but also gain critical visibility into file transfer performance, system issues and user activity.
Whether it’s identifying threats, troubleshooting failed transfers or ensuring accurate revenue recognition through verifiable delivery tracking, monitoring and audit logs deliver measurable business value. A secure file transfer platform like Thru empowers teams with the insight and control they need to protect data, streamline operations and support the bottom line.
Want deeper visibility into your file transfers? Explore Thru’s file transfer reporting and analytics capabilities »
